Hello, you are using an old browser that's unsafe and no longer supported. Please consider updating your browser to a newer version, or downloading a modern browser.
Hello, you are using an old browser that's unsafe and no longer supported. Please consider updating your browser to a newer version, or downloading a modern browser.
Published by Mike McNelis on June 1, 2024

In an increasingly digital world, maintaining good cyber hygiene is non-negotiable.
Here at Training Camp, we recognize the growing threat landscape and the need for robust cybersecurity practices.
This blog post will provide practical steps and essential tools to help secure your digital environment.
Cyber hygiene is about maintaining and improving your digital habits to ensure security and prevent data breaches. Think of it as the digital equivalent of personal hygiene. It’s about forming good habits to keep your digital environment clean and secure.

Statistics reveal that basic cyber hygiene can prevent up to 98% of cyber attacks. This tells us how impactful simple practices can be in shielding against major threats.
Understanding common cyber threats is the first step to effective cyber hygiene. Phishing attacks, for example, have surged, accounting for 32% of all data breaches in 2022, according to a report by Verizon. Phishing often targets individuals and employees, tricking them into revealing sensitive information. It’s crucial to educate yourself and your team to recognize phishing attempts.
Another significant threat is outdated software. Unpatched software vulnerabilities are like open doors for cybercriminals. Regular updates can eliminate these vulnerabilities. Data from Microsoft shows that more than 70% of successful breaches could be prevented through proper patch management.
Also, weak passwords remain a major vulnerability. Use strong, unique passwords for different accounts and consider using a password manager to simplify this process. Enabling multi-factor authentication (MFA) adds an additional layer of security.
Real-world examples underscore the importance of cyber hygiene. In 2021, a ransomware attack on Colonial Pipeline led to fuel shortages and highlighted weaknesses in critical infrastructure. This incident underscores the importance of timely software patches and robust defense mechanisms.
Another example is the infamous WannaCry ransomware attack in 2017, which affected over 200,000 computers in 150 countries. The attack exploited a known vulnerability in Windows operating systems, emphasizing again the necessity of regular updates.
Studies have shown that phishing-resistant multifactor authentication can prevent 99.9% of attacks on accounts. Implementing strong cybersecurity practices like these not only protects individual users but also helps safeguard larger networks and systems.
For more insights on common threats and how to defend against them, check out biggest cyber threats.
Making a habit of following these practical actions will significantly enhance your cyber hygiene and reduce your vulnerability to cyber attacks.
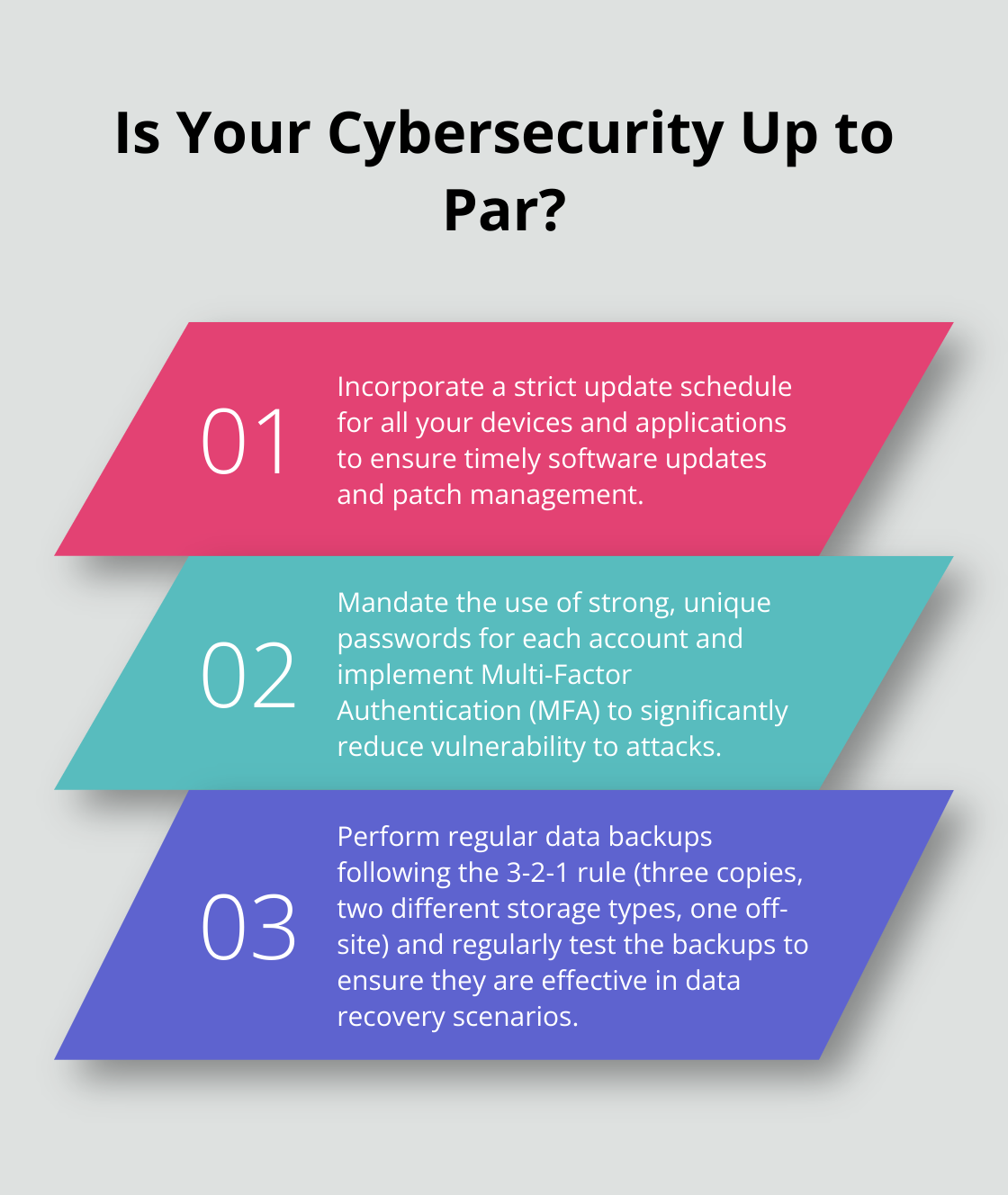
Keeping your software up-to-date is non-negotiable. Unpatched vulnerabilities act as open invitations for cyber attackers. Data from Microsoft reveals that more than 70% of successful breaches result from outdated software. Incorporate a strict update schedule for all your devices and applications. Automate whenever possible to reduce human error. Cybercriminals exploit even short delays, so timely updates are crucial.
Weak passwords are among the most common vulnerabilities. A strong password policy should mandate complex, unique passwords for each account. Tools like password managers can simplify this process, making it easier to maintain high security standards. Multi-Factor Authentication (MFA) adds an indispensable layer of protection. Case studies indicate that phishing-resistant MFA can prevent 99.9% of attacks on accounts. Encouraging your team to adopt these practices will significantly bolster your cyber defenses.
Data loss can be catastrophic. Regular data backups are essential for fast recovery after a cyber incident. Aim to follow the 3-2-1 rule: three copies of your data, two different storage types, and one off-site backup. Reliable backup solutions can involve cloud services or physical storage options. Regularly test your backups to ensure they work when needed. A robust backup strategy not only helps in data recovery but also mitigates the impact of ransomware attacks. For more insights on ransomware readiness, refer to assessing ransomware defense.

By integrating these practices into your daily routine, you’ll significantly reduce your exposure to cyber threats and improve your overall security posture.
Using reliable antivirus and anti-malware software is non-negotiable in achieving robust cyber hygiene. According to AV-Comparatives, top performers such as Bitdefender and Kaspersky reliably detect and block more than 99% of threats. Regular scanning with these tools identifies and removes any malicious software from your systems. Ensure that your antivirus software is always up-to-date to combat the latest threats. Malwarebytes is another effective option, offering comprehensive protection against a range of malware, ransomware, and spyware.
Effective network security tools are vital for monitoring and protecting your network. Firewalls like Cisco’s Adaptive Security Appliance (ASA) provide robust defense by filtering incoming and outgoing traffic. For smaller setups, tools such as pfSense offer an open-source solution that delivers strong security features. Implementing Intrusion Detection Systems (IDS) like Snort can also significantly enhance your security posture by identifying and alerting you to potential threats in real-time.

Network monitoring solutions like SolarWinds help you maintain visibility over your network, making it easier to spot unusual activities that could signal a security issue. These tools facilitate a proactive stance against cyber threats by analyzing traffic and detecting anomalies.
Educating yourself and your team is crucial. Security awareness training can drastically decrease the likelihood of successful phishing attacks. A study by KnowBe4 found that phishing test failure rates dropped by an average of 87% after one year of implementing regular security training. Programs like the SANS Security Awareness Training provide comprehensive modules tailored to various levels of cyber expertise.
Incorporating resources from trusted organizations, such as the Cybersecurity & Infrastructure Security Agency (CISA), can further enrich your knowledge base. Continuous learning and training create a culture of vigilance and awareness, fortifying your cyber hygiene practices. Accessing tailored workshops like those offered in the cybersecurity strategy workshop can also build a strong, well-informed team.
Adopting these tools and continually improving through training significantly strengthens your cyber hygiene, providing a fortified defense against cyber threats.
Implementing good cyber hygiene practices is essential to maintaining a secure digital environment. Regular software updates, strong password policies, and robust data backup strategies are critical steps. Using reliable antivirus and anti-malware software, alongside network security tools, further strengthens your defenses.
It’s vital to be vigilant about the evolving threat landscape. Continuous education and awareness training can dramatically decrease the risk of cyber attacks. Embrace resources like those offered by CISA to stay informed.
We encourage everyone to adopt these cybersecurity measures. At Training Camp, we specialize in helping individuals and organizations enhance their cyber hygiene. Our award-winning IT certification programs and compliance training ensure you’re well-prepared to tackle cybersecurity challenges confidently. Protect your digital world with proactive and consistent cyber hygiene practices.
Back to All Posts